
SyntaxPhoenix DDoS Protection
Protect your applications with the modern DDoS protection from SyntaxPhoenix

Protection against DDoS attacks
Companies and their infrastructures are increasingly the target of DDoS attacks. DDoS attacks or distributed denial-of-service attacks are coordinated, targeted attacks on a server in order to overload it with a large number of requests so that it can no longer perform its normal tasks and the services hosted on it can no longer be reached. These failures can lead to immense damage to the company's image and loss of revenue due to the unavailable infrastructure.However, you can protect yourself against DDoS attacks in a targeted manner and filter them in advance using filter measures in the form of DDoS protection.
How the SyntaxPhoenix DDoS Protection works
In the case of SyntaxPhoenix DDoS protection, the traffic is already filtered by the DDoS protection before it reaches the server. Algorithms are used to distinguish malicious traffic from normal traffic generated by your users and filter them accordingly.The traffic from DDoS attacks is already discarded at the DDoS protection and thus does not reach your server.
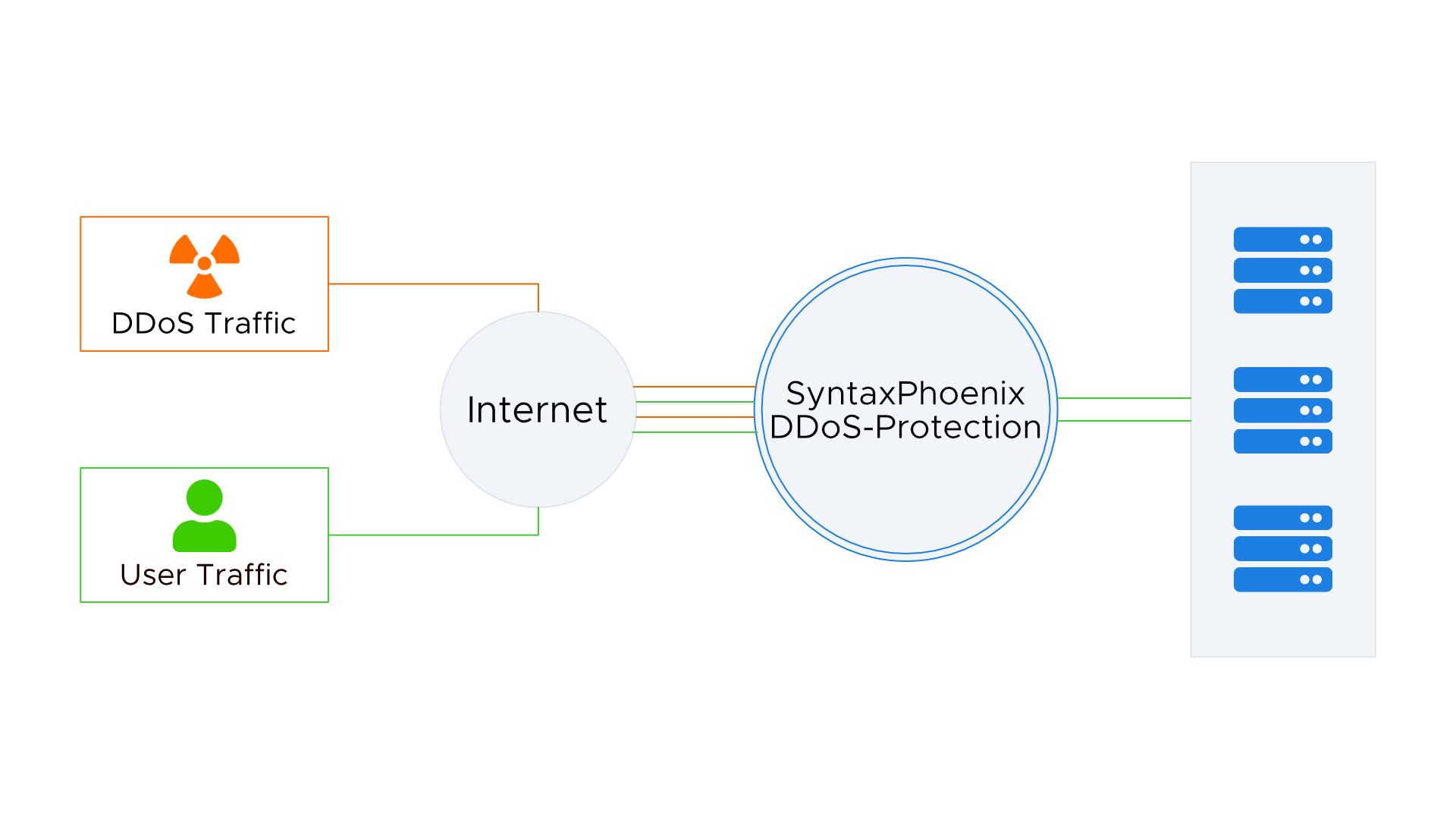
Contrary to many competitors, the SyntaxPhoenix DDoS protection is permanently active and permanently filters the traffic for potential DDoS attacks. In this way we can ensure that traffic from a DDoS attack, if it can be filtered, will not reach your server.
The SyntaxPhoenix DDoS protection relies on many filter methods for the best possible protection and uses multi-level filter pipelines with up to 28 filter levels. The SyntaxPhoenix DDoS protection is already prepared for amplification attacks, TCP floods, well thought-out Layer 7 attacks and other attack scenarios.
Thanks to our network being sufficiently connected to the outside world, we can fend off attacks of up to 750Gbit/s without the use of null routing.
Structure of the SyntaxPhoenix DDoS protection
The SyntaxPhoenix DDoS protection consists of a Netscout Arbor Sightline and several other in-house developments. With the help of this infrastructure, the SyntaxPhoenix DDoS protection is able to filter attacks of up to 750Gbit/s. A large number of attack methods are automatically recognized and mitigated.
An excerpt of the filterable attack types

Flood Attacks
Flood attacks are typical DDoS attack scenarios in which the attackers send increased traffic volumes to the affected systems.
TCPUDP
ICMP
DNS Amplification

TCP Stack Attacks
TCP stack attacks explicitly attack the handshake functionality of the TCP / IP stack.
SYNFIN
RST
SYN ACK
URG-PSH
TCP Flags

Fragmentation Attacks
Fragmenation attacks are based on the IP / ICMP fragmentation packets. The attackers send packets that cannot be defragmented and thus fill the memory of the server.
TeardropTarga3
Jolt2
Nestea

Application Attacks
Application attacks are explicitly aimed at the application layer and exploit weak points in applications.
HTTP GET floodsSIP invite floods
DNS attacks
